Our introduced localization framework showing the two offline phases
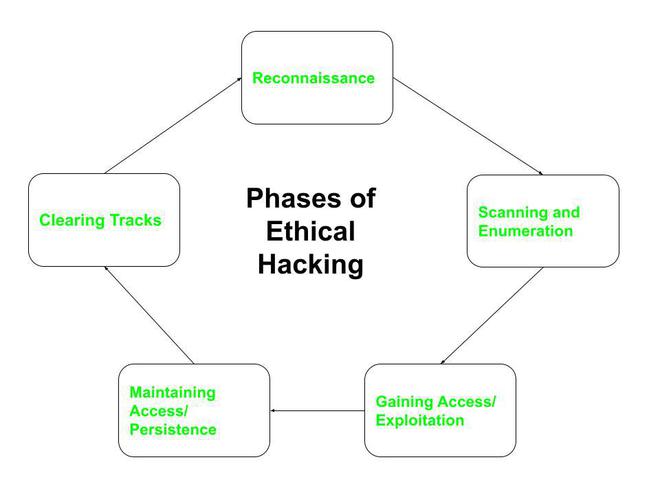
5 Phases of Hacking - GeeksforGeeks
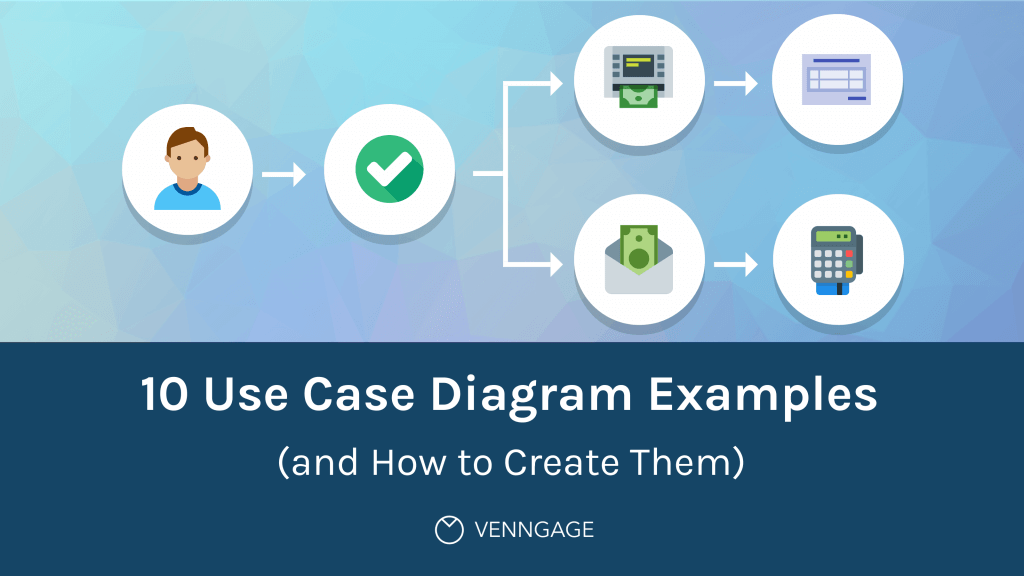
10 Use Case Diagram Examples (and How to Create Them) - Venngage

Why You Need a Localization Strategy, and How to Build One
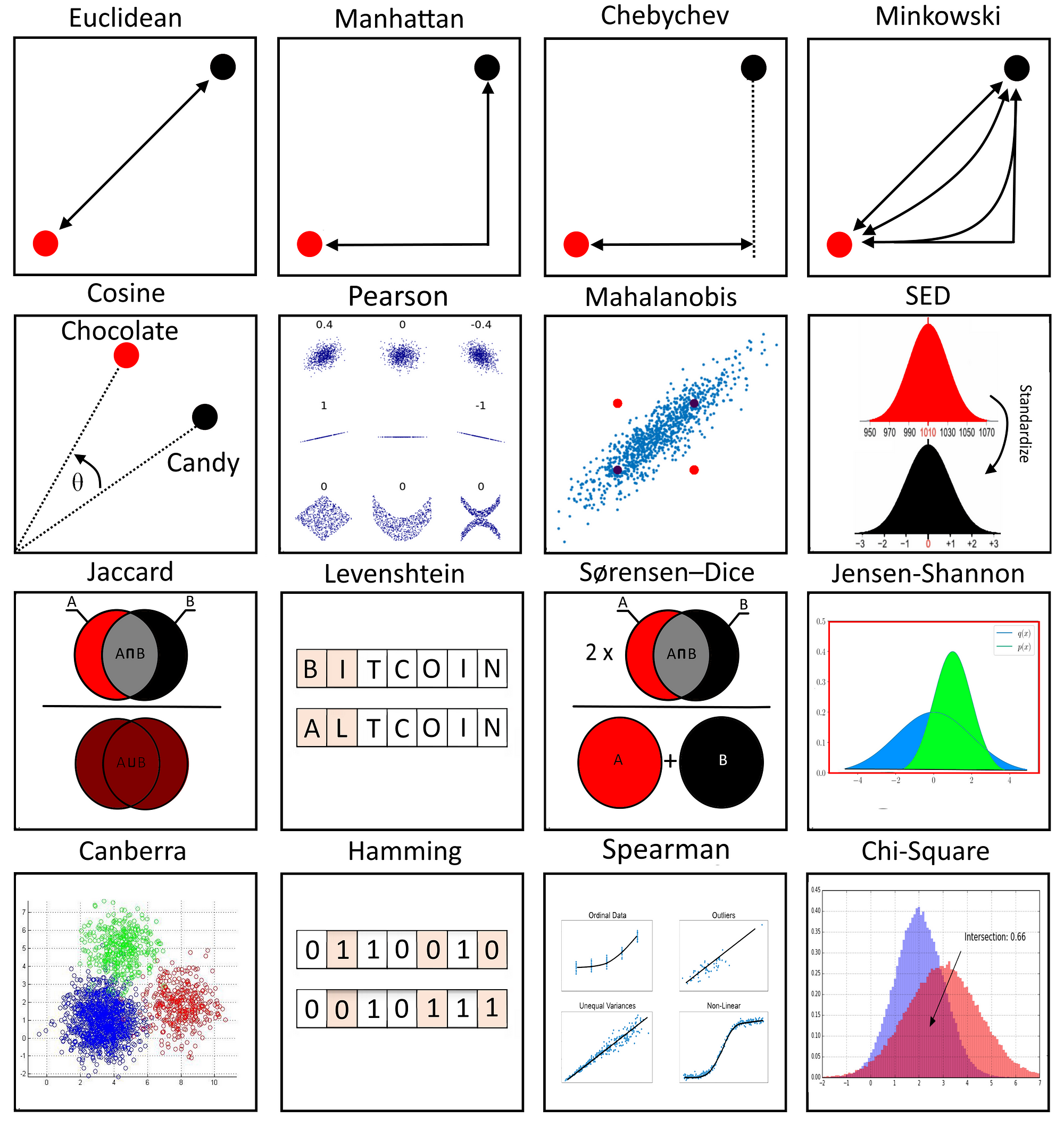
17 types of similarity and dissimilarity measures used in data science., by Mahmoud Harmouch
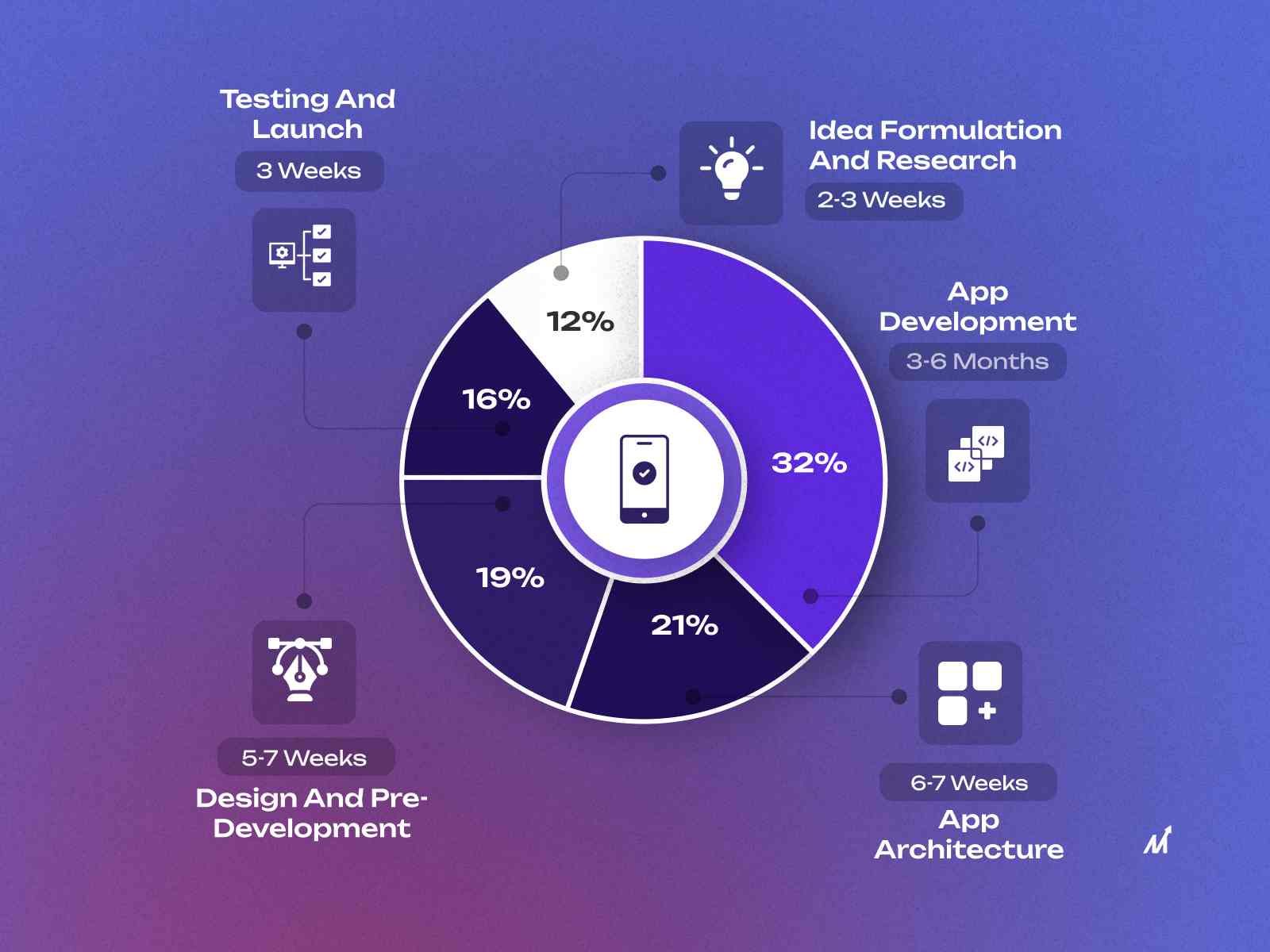
App Development Timeline - How to build it faster?

Nazanin RAHNAVARD, Associate Professor, Doctor of Philosophy, University of Central Florida, Florida, UCF, Department of Electrical Engineering & Computer Science
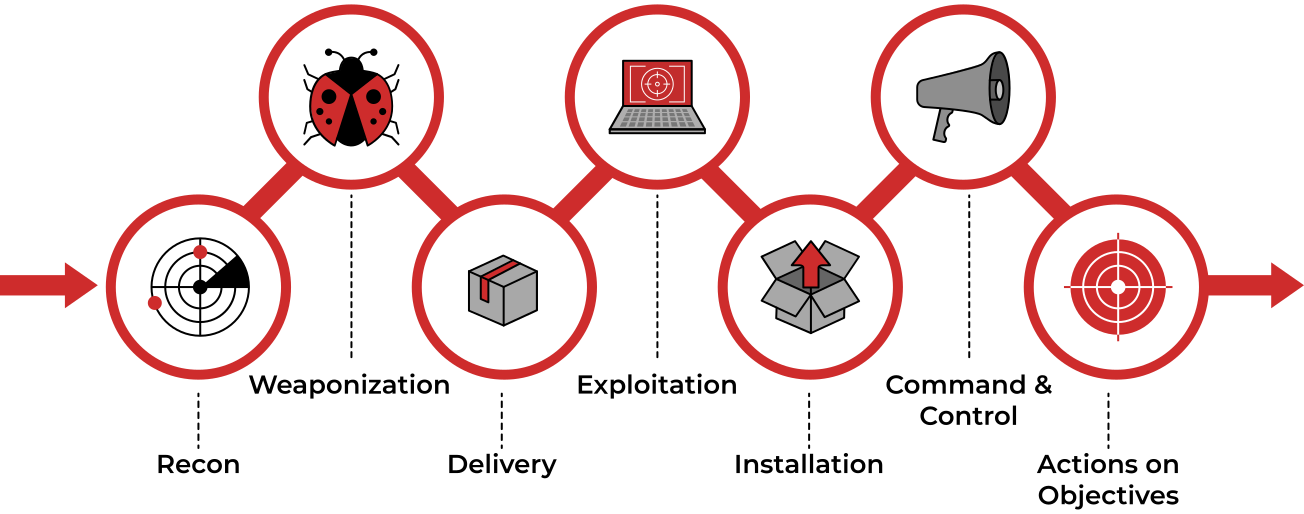
TryHackMe Cyber Kill Chain Room. The Cyber Kill Chain framework is

Unified Modeling Language (UML) Diagrams - GeeksforGeeks

Katarina VUCKOVIC, PhD Student, University of Central Florida, Florida, UCF, Department of Electrical Engineering & Computer Science

Katarina VUCKOVIC, PhD Student, University of Central Florida, Florida, UCF, Department of Electrical Engineering & Computer Science

In-Context Learning Approaches in Large Language Models

Run A Small Language Model (SLM) Local & Offline, by Cobus Greyling, Feb, 2024
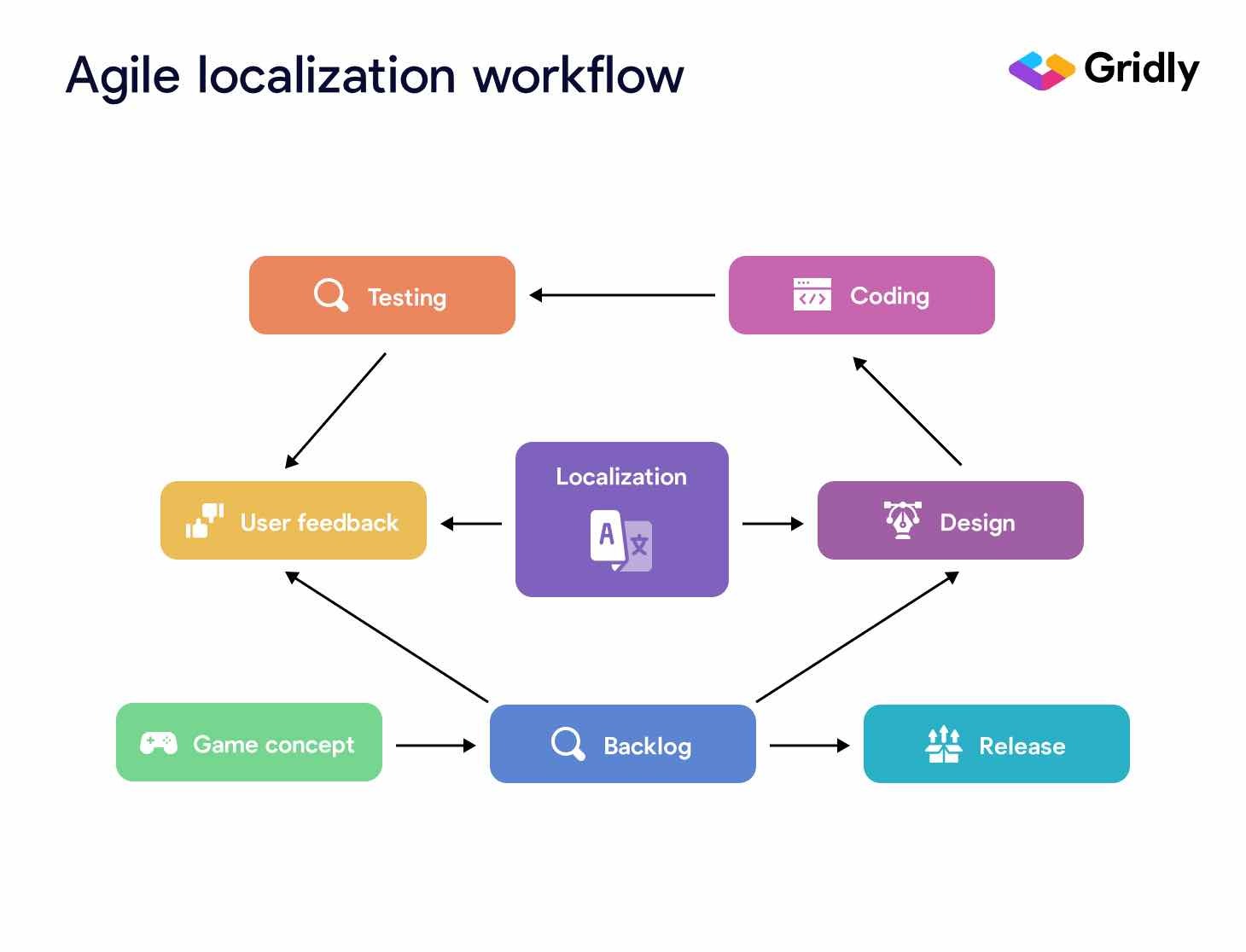
6 Steps to Efficiently Scale Your Localization Strategy

5 State Process Model in Operating System - GeeksforGeeks







