Attackers can force Echos to hack themselves with self-issued commands

Popular “smart” device follows commands issued by its own speaker. What could go wrong?

Technical Advisory: Pulse Connect Secure – RCE via Uncontrolled Gzip Extraction (CVE-2020-8260), NCC Group Research Blog

A survey on security analysis of echo devices - ScienceDirect

2023 IJCAI YES inaugurated at ECNU With Keynote Speeches about the field of AI-East China Normal University
What is a Cyber Attack? Definition and Related FAQs
How would you measure the success of Echo?, echo alexa

Hacking Is Not A Crime. It's An ART of Exploitation.

Securing Developer Tools: A New Supply Chain Attack on PHP

New Loop DoS attack may target 300,000 vulnerable hosts

s Echo smart speakers can be hacked to issue self-commands – The Cybersecurity Daily News
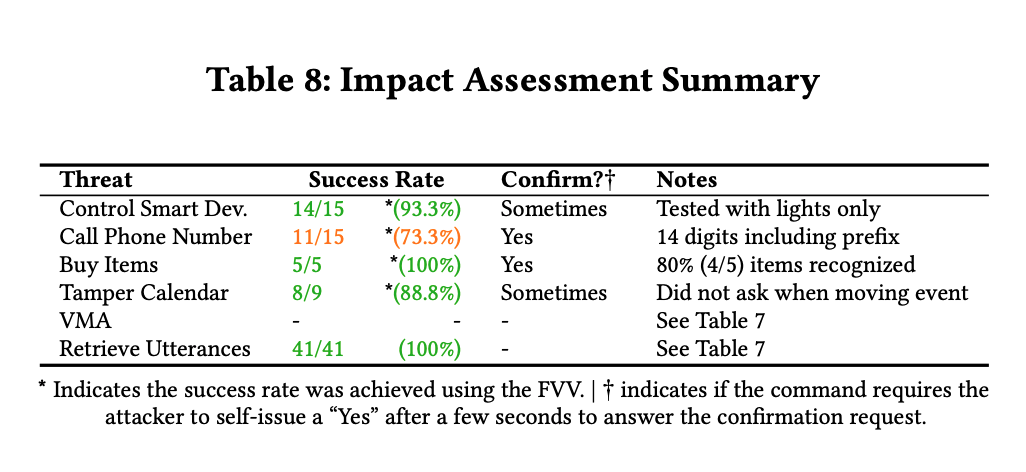
Attackers can force Echos to hack themselves with self-issued commands

The inside story of the world's most dangerous malware - E&E News by POLITICO

A survey on security analysis of echo devices - ScienceDirect

Cyberattacks Are a Nuisance, Not Terrorism

GitHub is under automated attack by millions of cloned repositories filled with malicious code
Mapping vulnerabilities in echo using alexa skills







