Layer 8 Hacking - Linking the OSI Model with the NIST Triangle

Layer 8 Hacking can be defined as hacking above and beyond the technical layers; hacking by targeting the user, the business processes, or the organization i

Major Network Fundamental is Explained. OSI Model and Its Security

Layer 8 Hacking - Linking the OSI Model with the NIST Triangle

Internet of Things Security and Privacy
Networking Basics: The OSI Model

Ethical hacking for IoT: Security issues, challenges, solutions

The 8 Layers of the OSI.pdf

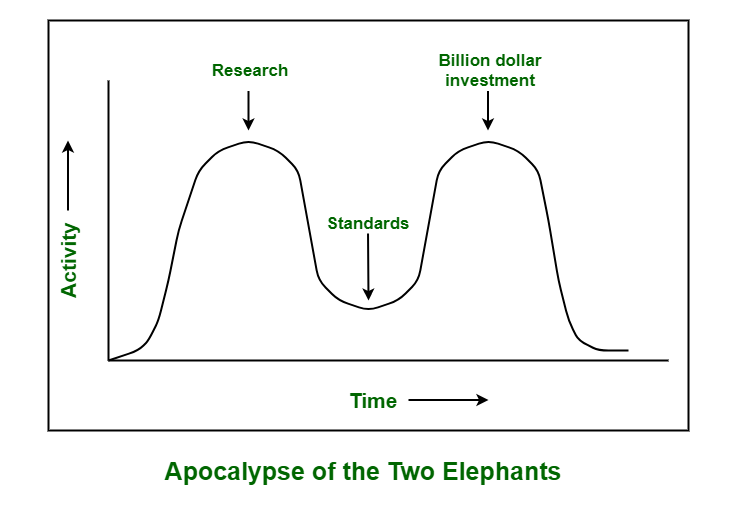
PDF) New Trends in Network Cyber Security (Part 1) (Paperback)
Applied Sciences, Free Full-Text
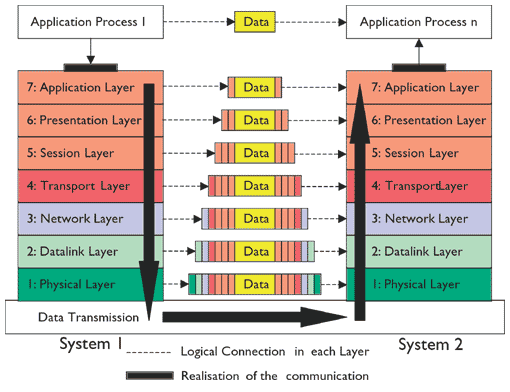
The Open Systems Interconnection model is a conceptual model that characterises and standardises the communication functions of a telecommunication or
Cyber security - Hacker Networking Skills - OSI Model vs TCP/IP
Critique of OSI Model and Protocols - GeeksforGeeks

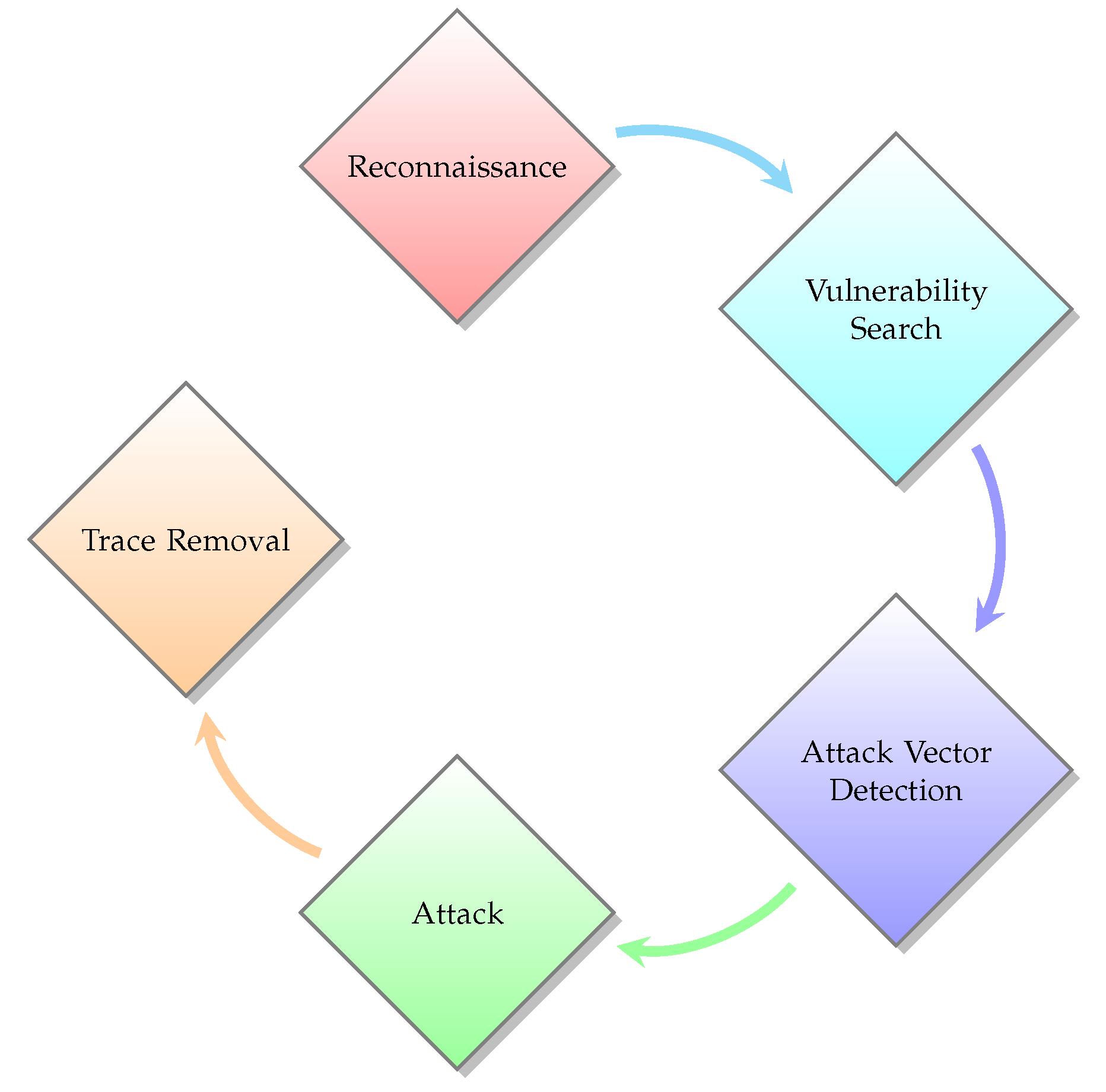
OSI Reference Model Penetration Testing

The OSI Model Explained in Easy Steps
osi-model- Penetration Testing

Cyber Terrain”: A Model for Increased Understanding of Cyber Activity







