Computer Systems Security (Cs-426), PDF

CSS Final2020 - Free download as PDF File (.pdf), Text File (.txt) or read online for free.
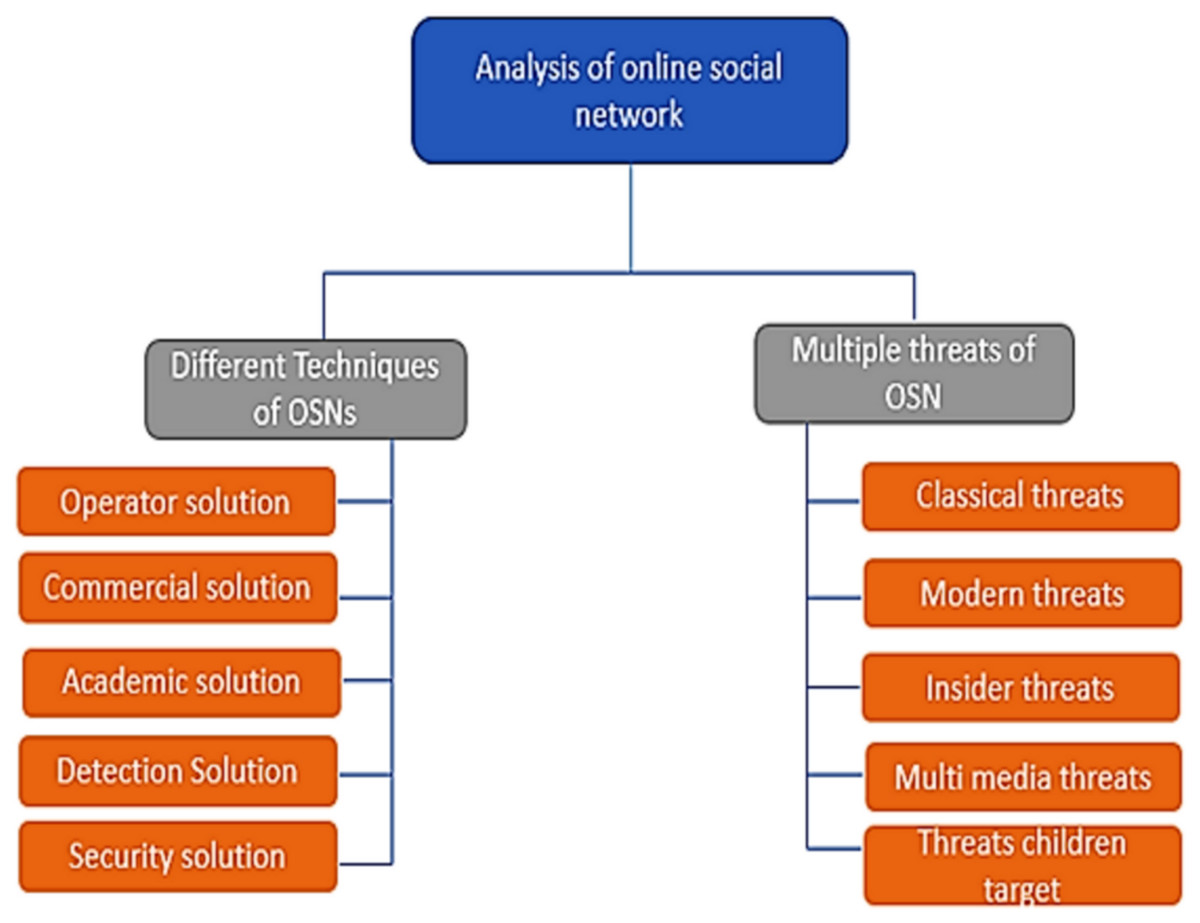
A comprehensive review of security threats and solutions for the online social networks industry [PeerJ]

c How secure is your approach in part b What are some possible attacks on your
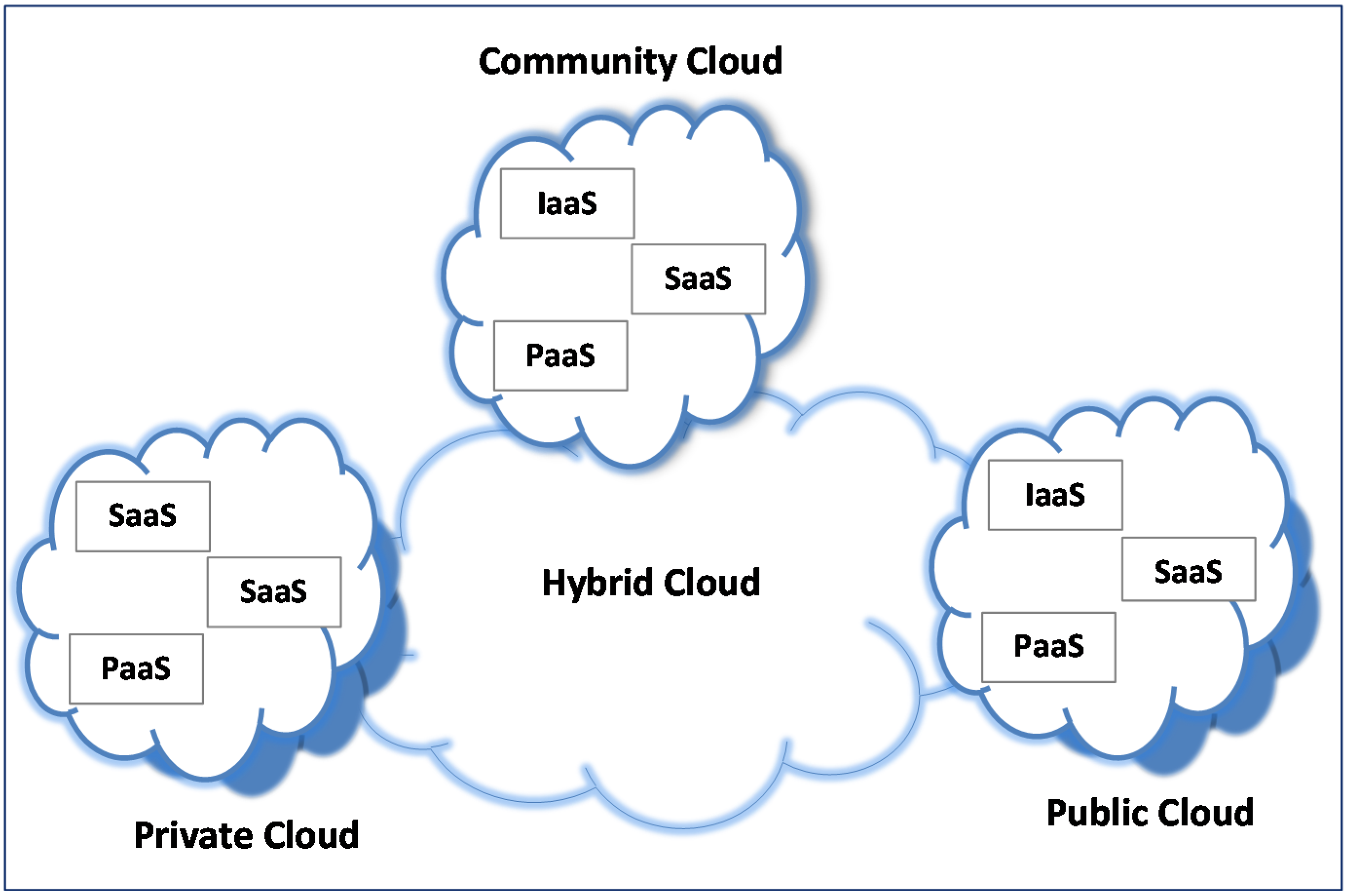
Computers, Free Full-Text

Cyber-Physical Systems Security
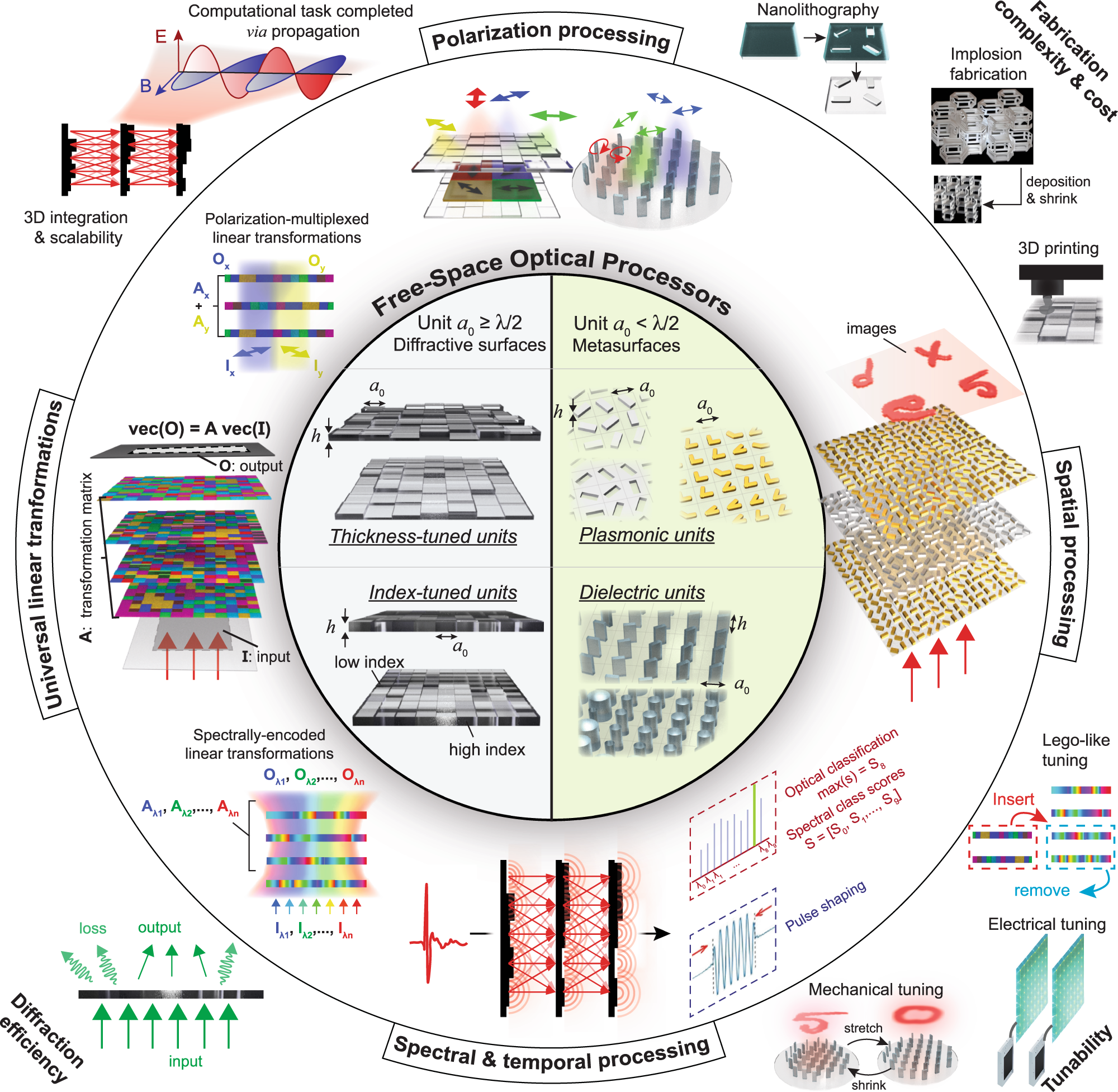
Diffractive optical computing in free space
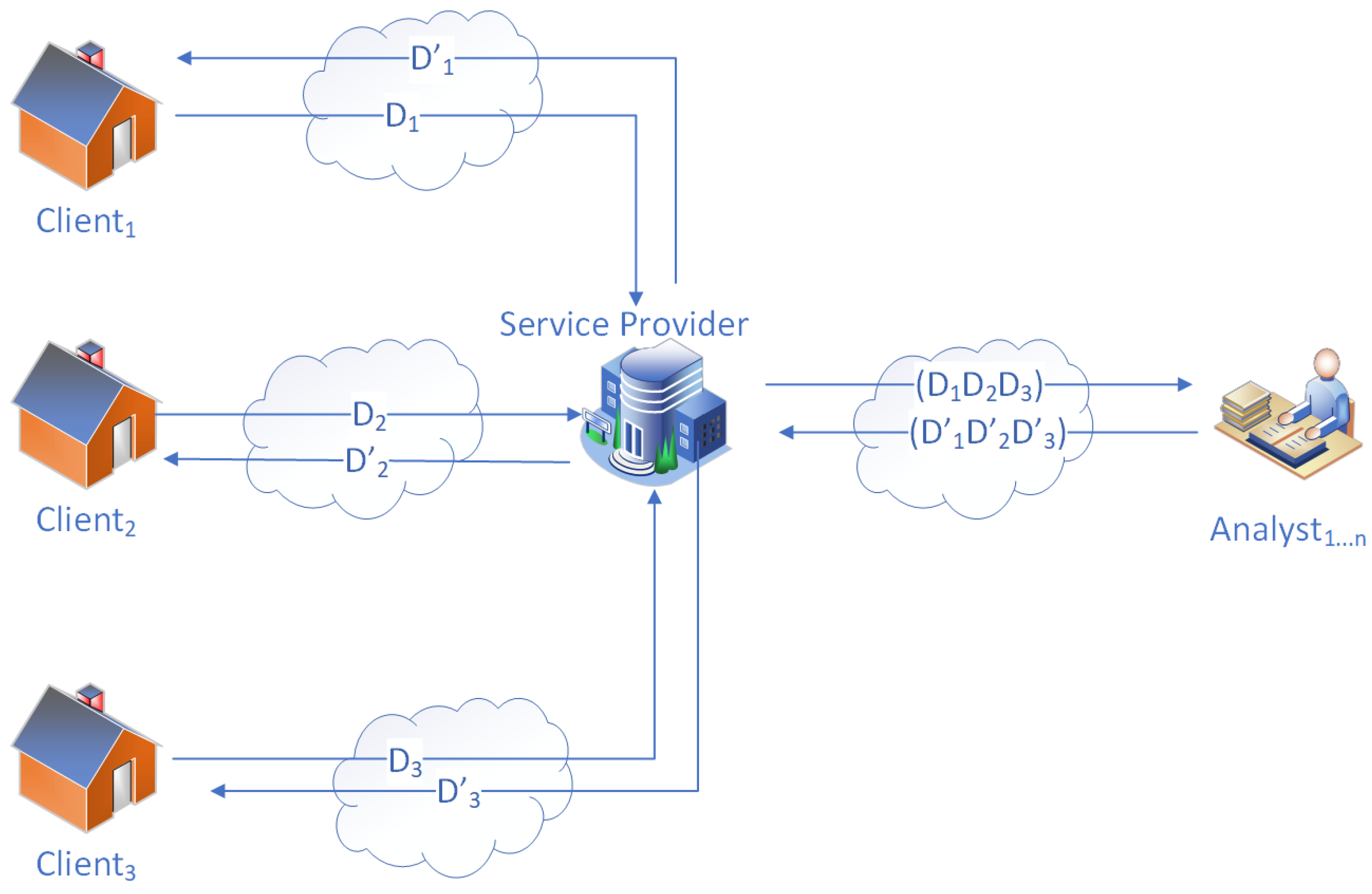
Sensors, Free Full-Text
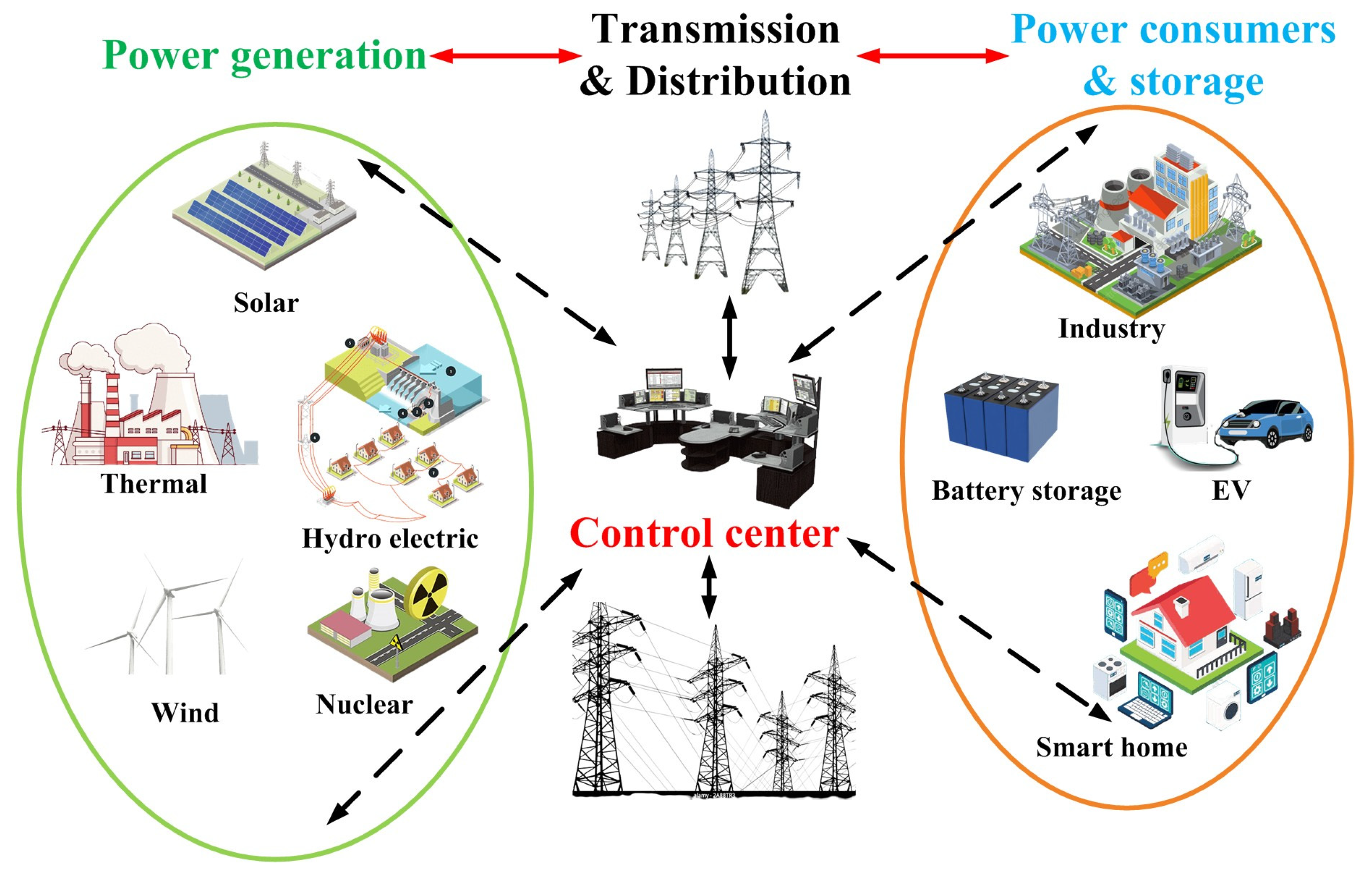
Energies, Free Full-Text

CS 651 : Computer Systems Security Foundation - Colorado Technical University
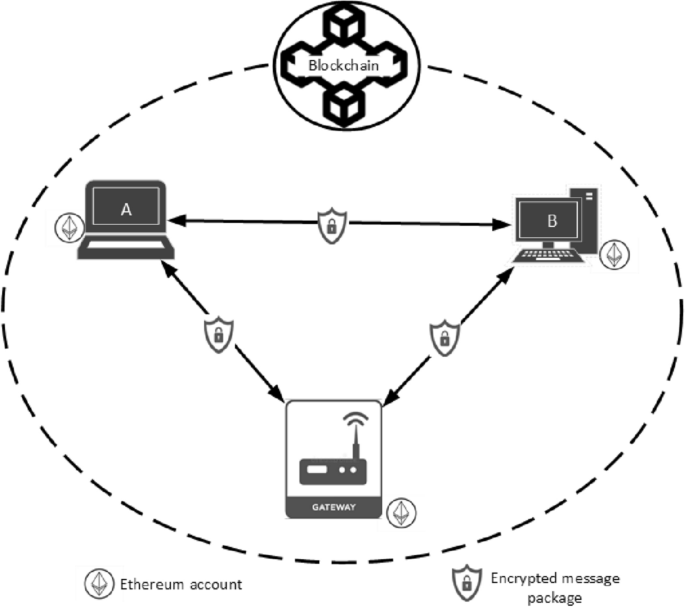
Blockchain-based privacy and security model for transactional data in large private networks

Effects of socioeconomic and digital inequalities on cybersecurity in a developing country

CS 426 : Computer Security - Purdue

CS 426 : Computer Security - Purdue

CS 426 : Computer Security - Purdue

Multiple Approach Paths to Insider Threat (MAP-IT): Intentional, Ambivalent and Unintentional Insider Threats







